![]() This information is provided for experienced users.
This information is provided for experienced users.
Remote access trojans are a menace to the Internet and a very high risk to all Internet users. Unlike worms and viruses, trojans almost always have a human directly behind them, who controls the trojan to take ownership of the target computer(s). At DiamondCS we've been researching trojans and developing countermeasures intensively for over half a decade, and our TDS anti-trojan system (http://tds.diamondcs.com.au) has been regarded by experts as the most comprehensive anti-trojan system available. The anti-trojan advances we've made in TDS have flowed into Port Explorer, so Port Explorer isn't just a socket explorer/analysis tool - it's actually a very powerful anti-trojan tool.
Nearly all trojans have one thing in common - they sit alive on your computer, running in the background as an invisible process (no windows, no taskbar icons, or anything visible on-screen), with a socket listening on a port (usually TCP). It's these characteristics that Port Explorer
zeros in on.
When Port Explorer finds a socket (this does not apply to '-NETSTAT-' sockets), it examines the parent process to determine if the process is displaying anything visible on-screen. If the process has nothing on-screen, Port Explorer will highlight the socket in a different
color (red by default). This does not necessarily mean that the process is a trojan, but it does mean that the process is running hidden and is using sockets so it is worthy of further investigation.
This image is an actual screen capture of Port Explorer taken on a Windows 2000 system that was infected with the common remote access trojan
"NetBus":
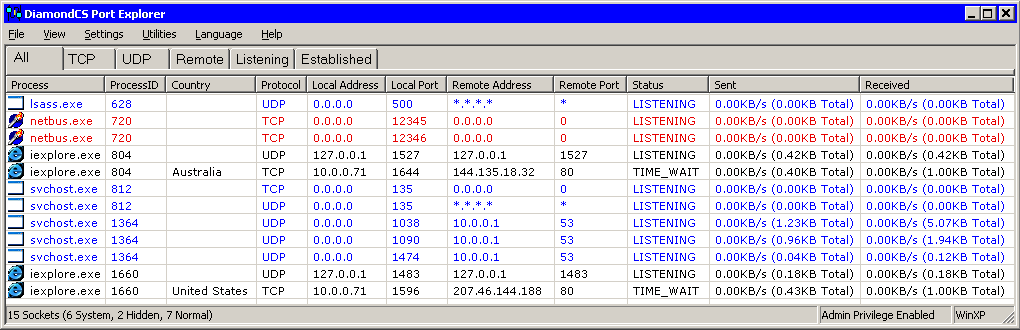
Port Explorer has determined that the process doesn't have any visible characteristics, so consequently the process has been highlighted in red. You can view more information about the file by right-clicking on the process and selecting "What is <process>?". The Status column shows that the process has two listening sockets. The socket listening on TCP 12345 is the main port that the trojan uses for communications. The second port (TCP 12346) is used for data transfer (files,
screen captures, etc), some trojans will listen on only one port at a time.
Terminating a trojan...
Now that we've identified the trojan, terminating it (killing its process) is simply a matter of right-clicking on the process and going to the Process submenu. Then simply press "Kill Process". If the attempt to kill the process fails, you'll be alerted with a messagebox. You won't see any message if the kill succeeds but you will notice the sockets belonging to that process disappear from the list. Now that the trojan process has been terminated, you can delete the file (d:\winnt\patch.exe in this case).
Advanced techniques for experienced users
These
techniques do not apply to '-NETSTAT-' sockets.
Neutralising a trojan...
Without terminating the process, Port Explorer actually gives experienced users the capability to render a trojan
virtually harmless yet still keep it alive by blocking it's capability to send data. This is ideal for honeypots that wish to record data that is received (for security or analysis purposes) but ensure no data is sent back. Blocks can be applied to either the entire process or individual sockets so you have complete control over send/receive capabilities of every process and socket on your system.
To do this, simply right-click on the socket you wish to impose a block on, and
go into the Process or Socket submenu (depending on whether you want to apply
the block to the socket or the entire process). Then it's simply a matter of
selecting "Disable Sending" or "Disable Receiving".
Sending/Receiving can be enabled/disabled using this method - the menus will
indicate if blocking is enabled by displaying a check beside the menu
item.
Spying on a trojan...
Spying on the communications of a trojan allows experienced curious users and
trojan analysts to document and analyse the protocol (the custom "language" that the trojan server and client speak to each other). This is best done with a neutralised trojan - experienced users may want to capture and analyse the data that is sent to the trojan socket. This is easily done simply by right-clicking on the desired process, going to the Process or Socket submenu, and selecting "Enable Spying". All data that is then sent/received by that process or socket is captured by Port Explorer and saved to a
log file. The log file can be viewed by the Socket Spy utility, available in the Utilities menu.
For more information, see Packet-sniffing with Socket
Spy